So my sister sent me an email as there were problems at work, as luck had it she was out of the office when she got this from bookkeeping.
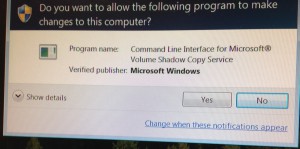 She couldn’t make heads nor tails of it. To be honest, I have been working most of the versions of Windows and this sounded pretty odd to me. The user kept pressing no but the dialog kept coming back. When my sister got back to the office she ran malwarebytes to check out the situation.
She couldn’t make heads nor tails of it. To be honest, I have been working most of the versions of Windows and this sounded pretty odd to me. The user kept pressing no but the dialog kept coming back. When my sister got back to the office she ran malwarebytes to check out the situation.
ransom.teslacrypt
Wow, so it seems like they have managed to get the teslacrypt virus. Not just any virus, but something that encrypts your files and then they want you to pay them to decrypt them. Traditionally there is no honor amongst thieves, so it is in doubt if they would hold up to their end and actually decrypt the files even if they were paid. I am not going to infect my pc to test that hypothesis.
How did this happen
I was kicking this around with my colleague and so we were wondering just what naughty web site was being surfed to get such a virus. It is a small office, so there is not much in the way of restrictions.
Perhaps to ensure this doesn’t happen again, should they install a proxy server? Do they need a different firewall solution? None of the users have administrator privileges. Is there something was overlooked?
Soul searching was done and a lot of questions were asked in addition to checking out the machine itself. It turns out that the reason why this happened was a lot simpler than Robert was hitting the porn sites on his lunch break.
It seems that Sally in bookkeeping received an email from an unknown person with an attachment of an “invoice” to needing to be paid. So Sally clicked on the attachment which came up and within seconds she knew that there was nothing that they needed to pay, click click click. Closed the attachment and deleted the email. It was shortly after this email that the odd behaviors started to occur.
There have been some good analysis of this virus such as this one. That explains the deletions of the shadow copy that were being displayed.
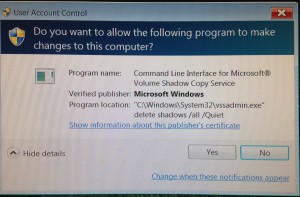 From the breakdown about how this virus worked, it was really well done – with an evil intent – but well programmed none the less.
From the breakdown about how this virus worked, it was really well done – with an evil intent – but well programmed none the less.
Lessons learned
There is no hard and fast rules for common sense, but easy does it, or look before you leap sound like a good advice.
I get a questionable emails every few days just like everyone else. What do the these emails want?
- click on this link to see sexy photos
- click on the attached photo
- check out my overdue bill
- bank transfer problems statement
- my travel itinerary
My favorites are the attachments with the names crafted for people who are only paying superficial attention to what is attached.
invoice-26282.pdf.exe
prom_picures.jpg.exe
The main lesson should be that you cannot click on just anything that is attached to your email. This is true if this is from unknownperson@sketchydomain.cj or your mom. It is possible for some of these virus’s to send out emails from your account to your friends in your contacts.
If the email doesn’t sound like it came from your friend or your family member, cast a skeptical eye on it. Don’t open the attachment, make a phone call send an email of your own asking about the email you received. If in doubt, simply delete it.
Final thoughts
You cannot be careful enough when surfing, opening emails, or running new programs. Below is a small list of some best practices to help keep your computer running virus free.
- Disable Outlook previews
- Ensure that all security updates and patches are installed
- Keep your software up to date with the latest versions
- Use Anti Virus sofware
- Think before you click on links or attachments
- Think before downloading new programs or utilities
- Disable autorun
- Use hardware firewall
- Company should use a proxy server

