In a previous article I described how you can use ecryptfs to secure your partition on your computer. It was a cool solution that but it was only available on Linux and all of the setup was done from the command line.
VeraCrypt is a encryption program which can be used to encrypt a partition or to create a file container which becomes a encrypted file system. The file container unlike a partition can then be copied like any other file to other disks, to another USB stick or even to another computer. In addition to supporting both partitions and file containers it also provides a small GUI to assist in setting up partitions and for mounting them.
You can probably download a copy of VeraCrypt from a number of sources but the best would be from their webpage codeplex.com.
Verify downloaded file
Like any other open source software it is a good idea to verify no problems during the download and that the file has not been tampered with. Linux provides the sha256sum program to generate the hash that can be matched against provides list of hashes provided by VeraCrypt.
In addition to the file, you will need to either download the checksums or look them up from the site.
veracrypt-1.16-sha256sum.txt
aafacca9a600af5b8d66387718c984b8655905f72370bbd772baf90e57e85b7e VeraCrypt Setup 1.16.exe
f5c70ad7ea8dd660f62b9162f745728ccfad1d00e74b3a4eedccf6c3d92eb43f VeraCrypt User Guide.pdf
bfe147cb4c0a0e8ab47fa71ae0d3eec825f49548246da6e4a75a7b9b6250d78c VeraCrypt_1.16.dmg
6861e79eb7e662330fa2a304061ebfb6a56929a78d8f4841ed0449a553257e7a veracrypt_1.16_Source.tar.bz2
0a1c6b8165d78be62623194178a109bdd8f8b4dbcb6c24d8b15eba629f99ddaf veracrypt_1.16_Source.zip
81afbde794ea8ff426f4b5ecfe72269fbdc9b99bb759f42eaf54936d1a7dd1ba veracrypt-1.16-setup.tar.bz2
Simply run the sha256sum with the downloaded file as the first parameter.
> sha256sum veracrypt-1.16-setup.tar.bz2
81afbde794ea8ff426f4b5ecfe72269fbdc9b99bb759f42eaf54936d1a7dd1ba veracrypt-1.16-setup.tar.bz2
It just isn’t quite that simple in the windows world as no program for calculating these hashes are shipped with the operating system. Yet, it is easy enough to find one, install it and then use that.
For windows I downloaded the project quickhash. This is a really easy program that can calculate the hash for text, files, disks and a whole lot more. They even ship documentation. If you are a windows user, this just might be the package for you.
However, from the user manual provided there may be some confusion over the name. It is possible that other developers have also developed their own program with the same name.
Install Windows
VeraCrypt has a standard windows installer, which walks you through the entire process.
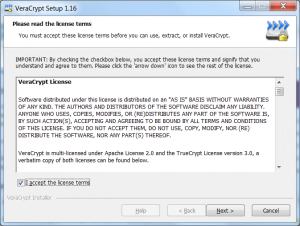
The VeraCrypt license that needs to be accepted
Install dialog
Another Install dialog
Dialog showing the current status of the install
Install Linux
The tar file containing VeraCrypt has been bzipped, and so you need to unzip it first. The bzip2 program is not as common of a choice for compressing data.
There have been a number of different analysis’s between gzip and bzip. The analysis can be summarized as gzip compresses faster but bzip has superior compression. The bzip speed/compression issue may be less and less important as the Linux kernel discontinued using it march 2013, it is possible that this will be the beginning of a trend.
| Command |
Description |
| bzip2 -d file.bz2 |
unpack the contents of the archive and delete the archive once that has been done. |
| bzip2 -dk file.bz2 |
unpack the contents of the archive and keep archive. |
The installation is just running a shell script. Simply run the script that is appropriate for the version of your operating system. They also provide two command line choices as well.
> bzip2 -d veracrypt-1.16-setup.tar.bz2
> ls -ltr
-rw-r--r-- 1 dock dock 16865280 Jan 13 23:28 veracrypt-1.16-setup.tar
>
> tar xvf veracrypt-1.16-setup.tar
> veracrypt-1.16-setup-console-x64
> veracrypt-1.16-setup-console-x86
> veracrypt-1.16-setup-gui-x64
> veracrypt-1.16-setup-gui-x86
>
> sh veracrypt-1.16-setup-gui-x64
>
Once you run this script, a few dialog’s will appear, simply click through the dialogs and enter the root password when prompted.
Install dialog
The VeraCrypt license that needs to be accepted
A reminder on how to uninstall VeraCrypt
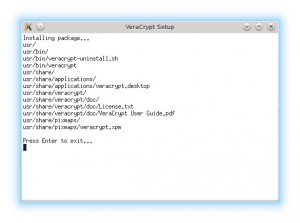
Installation log output
It takes only a few seconds to install the software, and then you are ready to run the software.
Setup
The documentation for veraCrypt is quite complete. It would be difficult to explain in few pages what they cover in quite a lot of detail in over 150 pages.
It is probably enough, to briefly describe the two different types of encrypted disks that would be created. The first is actually not really a disk but really a very small file system saved as a single file on your normal file system.
When this file is mounted with veraCrypt it becomes just like any other disk drive that can be written to. Because it is a single file, it could easily be copied to a USB stick, to another computer or to some sort of Internet storage device (cloud).
This is actually the best choice if you are not very comfortable with the lower levels of the disk drive such as partitions.
The second type of disk would be an actual disk partition. Instead of creating a file on an existing hard disk, a partition is selected and encrypted. This disk, when mounted, also behaves like any “normal” linux or windows file system.
When setting up your encrypted disk, you will be prompted for which encryption protocol amongst others things, but there is a rather harmless looking question that shouldn’t be overlooked.
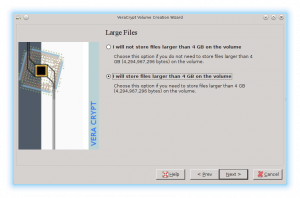
Do you want to store files larger than 4gb. It really depends on the type of data that you will be storing in this encrypted drive how you answer. Most data does not get anywhere near this size. A couple of exceptions might be some sort of raw video footage, or if you have ISO images from double layer DVD’s.
Another harmless looking question is if you plan on only accessing this encrypted disk from more than one operating system.
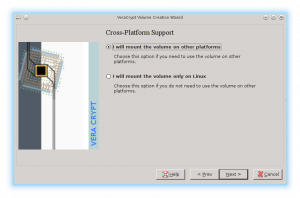
I suspect that quite a few Linux users still have a partition with a copy of windows that is used for some minor tasks. Setting this option will let you use veraCrypt on other platforms. This makes your encrypted partition accessible from both operating system. It can even be used as a method for transferring data between the two systems.
There is one small difference between veraCrypt and its predecessor truecrypt. When formatting the encrypted disk you simply select the file system, however, it is now possible to select NTFS even from Linux. Previously, the file systems available were only those supported by the running operating system. 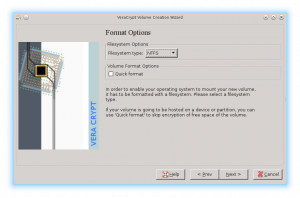
Limitations
The good news is that veraCrypt seems to be picking up where truecrypt left off. The solution provides a nice GUI which makes it really easy to mount encrypted files or partitions for even the most casual user.
The only real limitation that I encountered was that veraCrypt said it was compatible with truecrypt volumes. This might be the case, I did not have this experience.