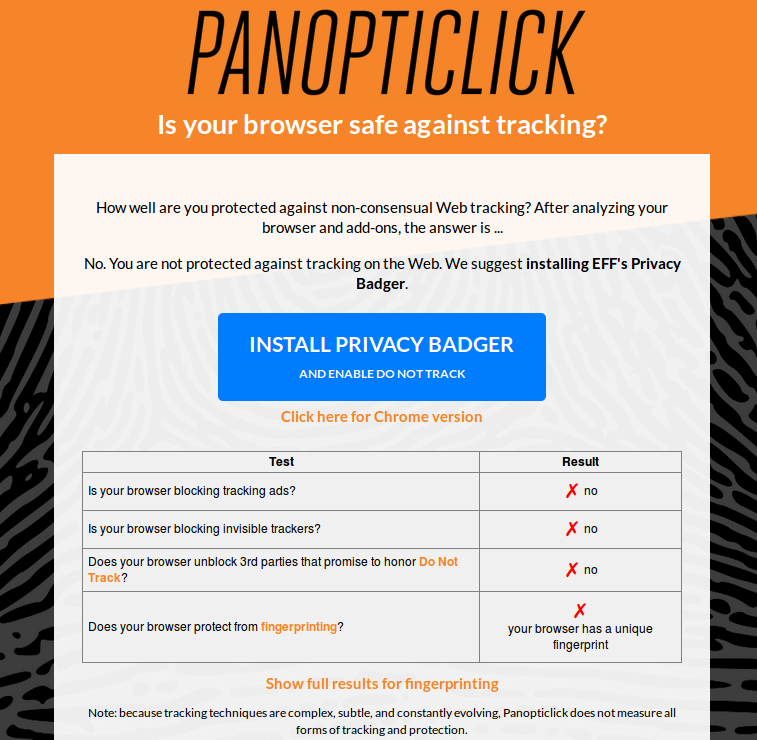
… well, that is a bit of an exaggeration. I owned a Samsung Galaxy S tablet which no longer worked. It had the darndest symptoms.
- doesn’t charge past 77 %
- takes a day to get to 77%
- spontaneously restarts shortly after startup
The plan was to take the tablet apart and try and repair it (despite not being a certified hardware repair person) After all, just how hard could it be?
The repair
The tablet wasn’t that old and was in otherwise perfect condition. The Internet implied that there were a couple of different parts that might solve the problem. I was hoping that simply replacing the usb port would be the problem.
https://www.amazon.de/gp/product/B01MFH19ZY/ref=oh_aui_detailpage_o02_s00?ie=UTF8&psc=1
It would have been perfect, the cost for a new port is less than 6 Euros. There are a number of really good youtube videos to help for replacing the usb port or how to replace the battery.
The hardest task was actually getting the back of the tablet off. The video for replacing the usb port makes it look pretty easy. In that video the back itself is simply pulled off and you don’t need any special tools for that.
It might be obvious from this picture but when I removed the back I actually pulled the screen out from the other side. This is actually quite similar to how it is removed in the battery video.
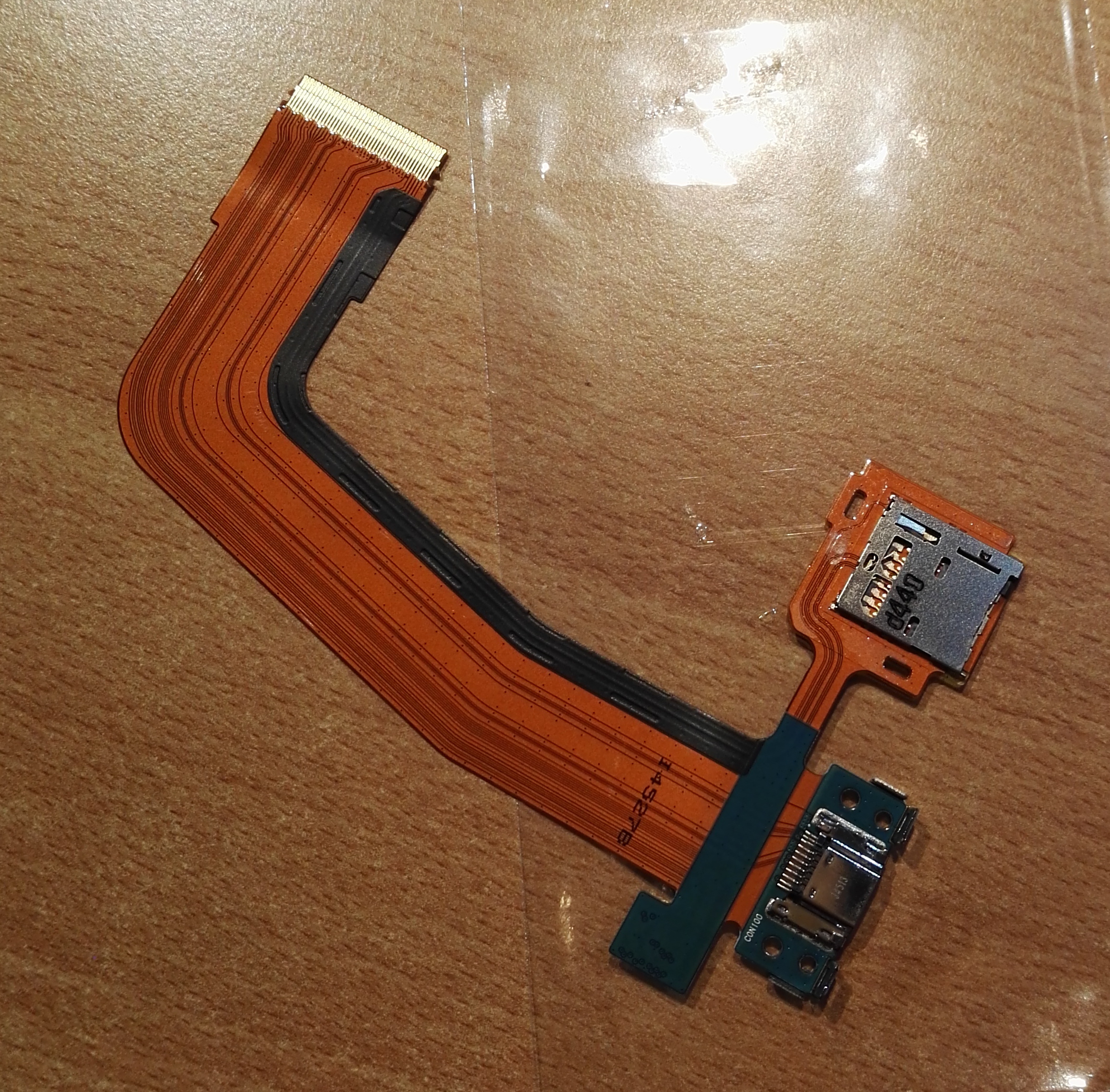
Removing the charger port is actually trivial, especially if you have removed the screen in the way that I did. The reason is that the back of the tablet is actually two parts. The first is a rim that goes around the tablet and holds both the screen in from one side and the back from the other side. This rim actually would make it a bit more difficult to get the port off.
Near the usb connector port is a two screws that hold the port to innards. Once the screws are removed a small bit of pressure and the port and the sdcard hold pop right off except for a small connector that also attaches to the board. The other end is a flat cable. The connector is slightly different as it flips up rather than slides to release the cable.
I had hoped that this six euro part would fix the problem but as it turned out this did not solve my problems. The new port did appear to work but once I removed the power cord from the tablet the device would barely make it to the startup screen.
https://www.amazon.de/gp/product/B00R1A0VK6/ref=oh_aui_detailpage_o00_s00?ie=UTF8&psc=1
The battery is actually even easier to remove than the charging port. There are four screws that held it in place and then the power cord snaps onto the board.
Lessons learned
Dealing with the insides of this particular tablet was actually very easy to work with. The most difficulties that I had was trying to get the cover off. I think that I must have been looking at a different video and it didn’t make the task easier.
I actually had a small set of tools that offered a number of possibilities but I used the small triangular pic.
The correct tool appears to have been this tool that I happened to overlook.
Everything works
For the low low cost of about 38 Euros I managed to get my tablet to work. I wouldn’t have done tried to take this apart if it hadn’t been non-functional and out of warranty. I don’t know how the repairable the newer Samsung tablets are but the older ones appear to be very repairable.